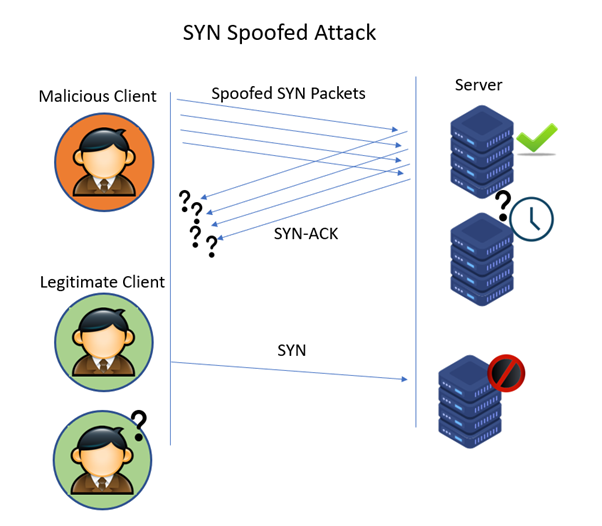
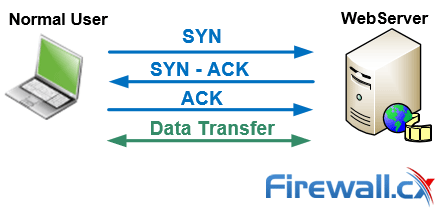
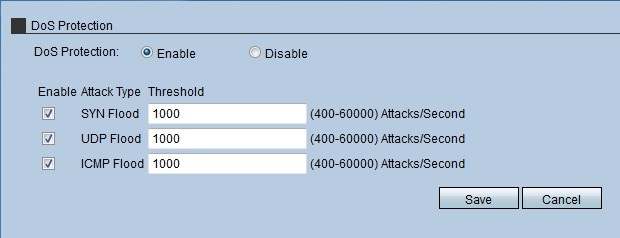
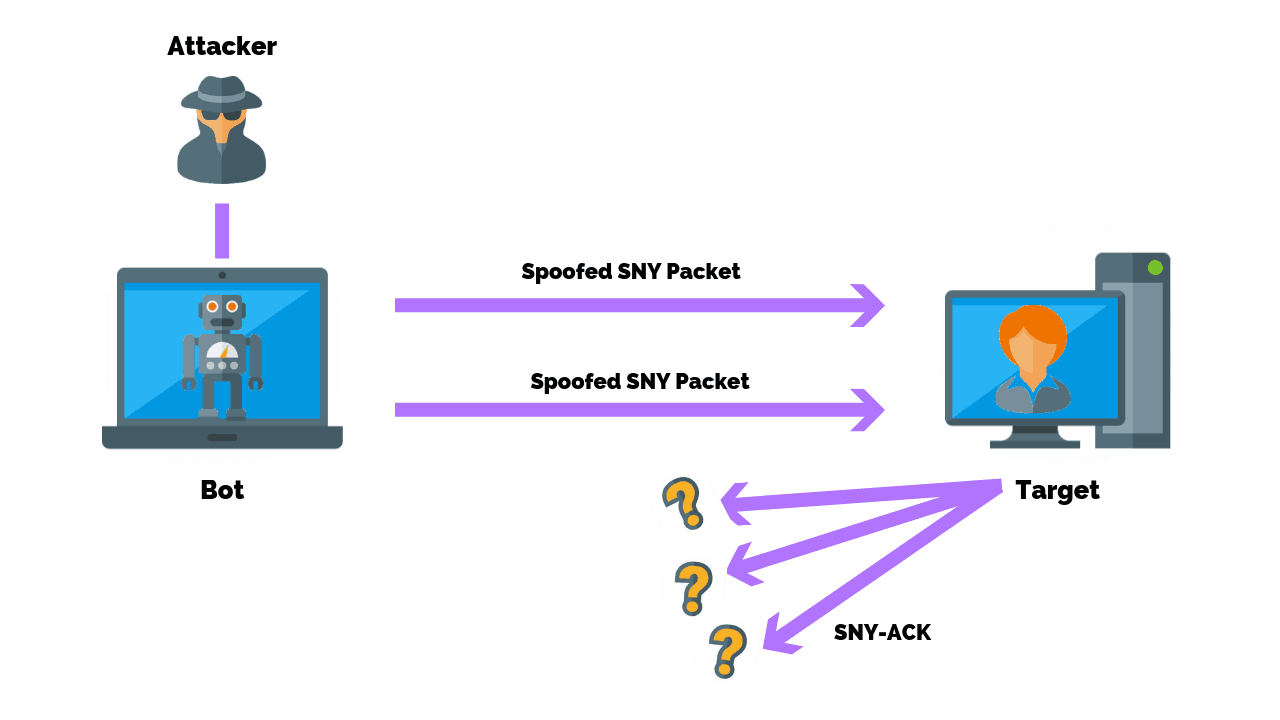
Detecting SYN flooding attacks based on traffic prediction - Wang - 2012 - Security and Communication Networks - Wiley Online Library

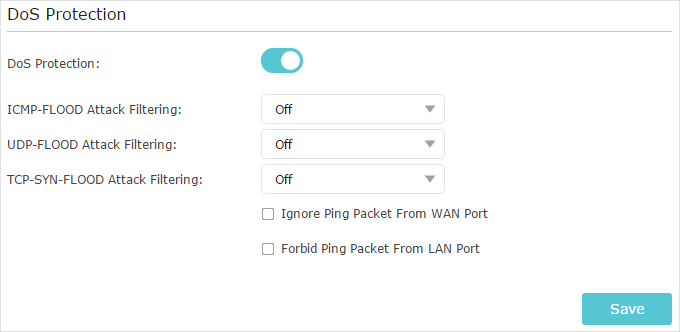
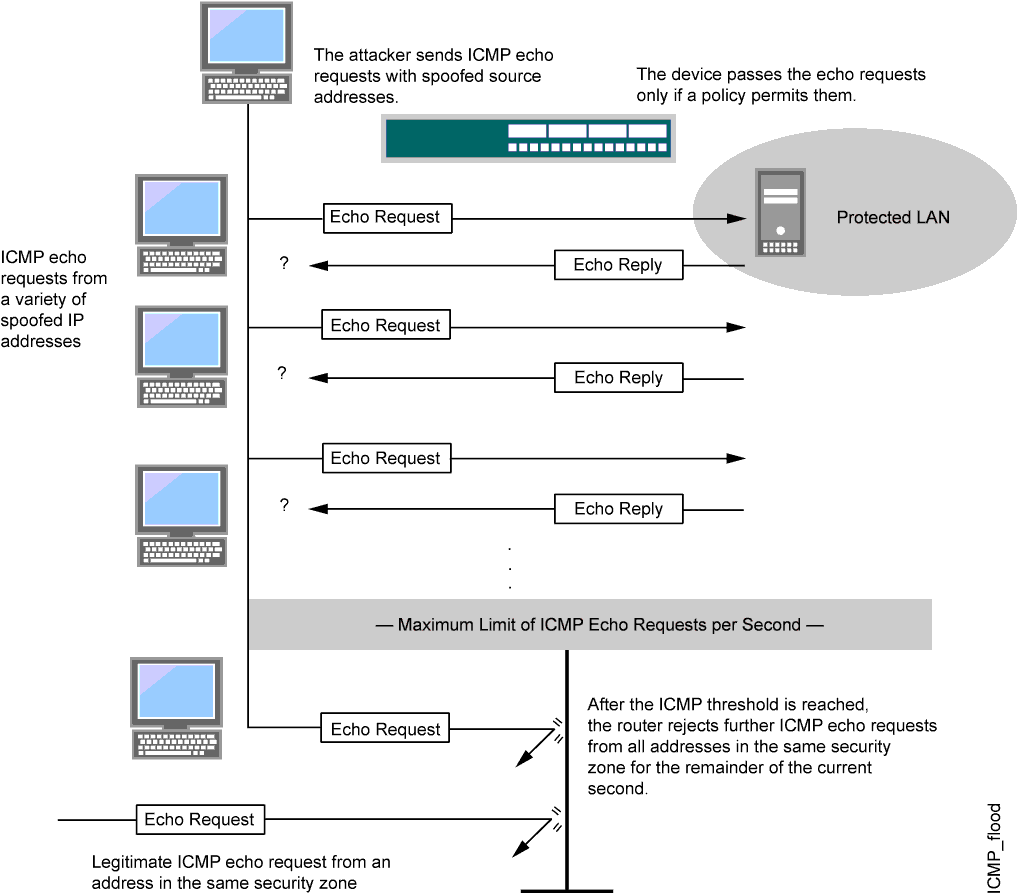
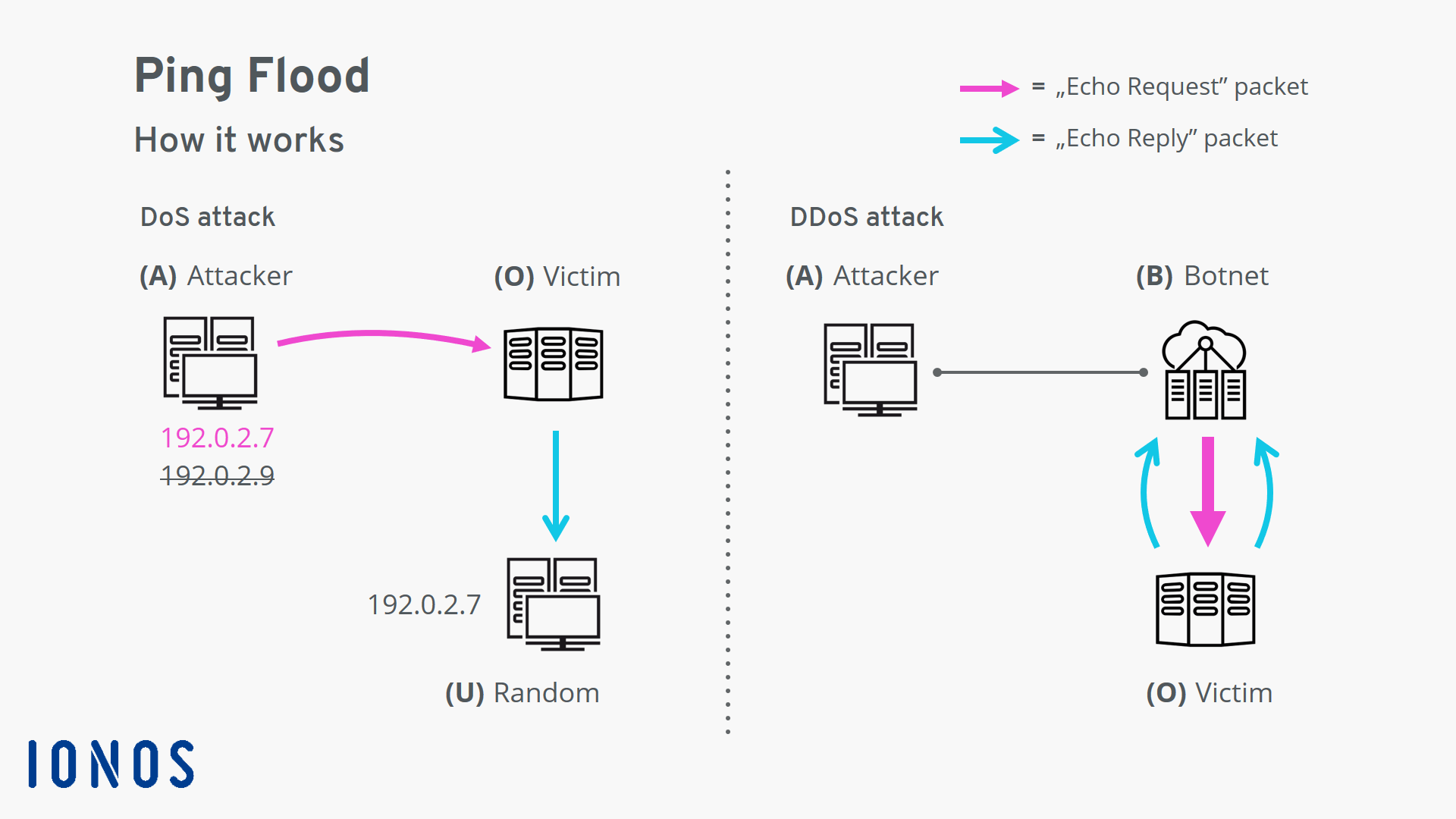
Troubleshooting Cases: SYN Flood Attacks Are Detected on a Network - AR Router Troubleshooting Guide - Huawei